7.10. Configuring dot1x
Overview
Function Introduction
IEEE 802 Local Area Networks are often deployed in environments that permit unauthorized devices to be physically attached to the LAN infrastructure, or Permit unauthorized users to attempt to access the LAN through equipment already attached.
Port-based network access control makes use of the physical access characteristics of IEEE 802 LAN infrastructures in order to provide a means of authenticating and authorizing devices attached to a LAN port that has point-to-point connection characteristics, and of preventing access to that port in cases in which the authentication and authorization process fails.
With 802.1X port-based authentication, the devices in the network have specific roles:
Client: the device (PC) that requests access to the LAN and switch services and responds to requests from the switch. The client software with support the follow the 802.1X standard should run on the PC. For linux system, we recommend the application which named “xsupplicant”.
Authentication server: performs the actual authentication of the client. The authentication server validates the identity of the client and notifies the switch whether or not the client is authorized to access the LAN and switch services. Because the switch acts as the proxy, the authentication service is transparent to the client. In this release, the Remote Authentication Dial-In User Service (RADIUS) security system with Extensible Authentication Protocol (EAP) extensions is the only supported authentication server. RADIUS operates in a client/server model in which secure authentication information is exchanged between the RADIUS server and one or more RADIUS clients.
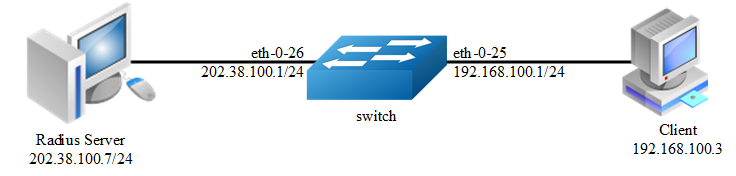
Switch (edge switch or wireless access point): controls the physical access to the network based on the authentication status of the client. The switch acts as an intermediary (proxy) between the client and the authentication server, requesting identity information from the client, verifying that information with the authentication server, and relaying a response to the client. The switch includes the RADIUS client, which is responsible for encapsulating and decapsulation the EAP frames and Interacting with the authentication server. When the switch receives EAPOL frames and relays them to the authentication server, the Ethernet header is stripped and the remaining EAP frame is re-encapsulated in the RADIUS format. The EAP Frames are not modified or examined during encapsulation, and the authentication server must support EAP within the native frame format. When the switch receives frames from the authentication server, the server’s frame header is removed, leaving the EAP frame, which is then encapsulated for Ethernet and sent to the client. We can enable dot1x on routed port and access port.
Principle Description
Reference to IEEE Std 802.1X- 2004.
Configuration
Basic dot1x configuration
step 1 Enter the configure mode
Switch# configure terminal
step 2 Enable dot1x globally
Switch(config)# dot1x system-auth-ctrl
step 3 Enter the interface configure mode, set the attributes of the interface and enable dot1x
Switch(config)# interface eth-0-25
Switch(config-if)# switchport mode access
Switch(config-if)# dot1x port-control auto
Switch(config-if)# no shutdown
Switch(config-if)# exit
Switch(config)# interface vlan 1
Switch(config-if)# ip address 192.168.100.1/24
Switch(config-if)# exit
step 4 Set the attributes of Layer 3 interface and set the Radius server
Switch(config)# interface eth-0-26
Switch(config-if)# no switchport
Switch(config-if)# ip address 202.38.100.1/24
Switch(config-if)# no shutdown
Switch(config-if)# exit
Switch(config)# radius-server host 202.38.100.7
Switch(config)# radius-server host 2001:1000::1
Switch(config)# radius-server key test
Switch(config)# exit
step 5 Exit the configure mode
Switch(config)# end
step 6 Validation
Switch# show dot1x
802.1X Port-Based Authentication Enabled
RADIUS server address: 2001:1000::1:1812
Next radius message ID: 0
RADIUS server address: 202.38.100.7:1812
Next radius message ID: 0
Switch# show dot1x interface eth-0-25
802.1X info for interface eth-0-25
portEnabled : true
portControl : Auto
portMode : Port based
portStatus : Authorized
Mac Auth bypass : disabled
reAuthenticate : disabled
reAuthPeriod : 3600
Max user number : 255
Current session number : 1
Accept user number : 1
Reject user number : 0
Guest VLAN : N/A
Assign VLAN : N/A
QuietPeriod : 60
ReqMax : 2
TxPeriod : 30
SuppTimeout : 30
ServerTimeout : 30
CD: adminControlledDirections : in
CD: operControlledDirections : in
CD: bridgeDetected : false
========================================
session 1: 1 - 0058.3f00.0001
----------------------------------------
user name : admin
abort:F fail:F start:F timeout:F success:T
PAE: state: Authenticated - portMode: Auto
PAE: reAuthCount: 0 - rxRespId: 0
BE: state: Idle - reqCount: 0 - idFromServer: 5
Enable dot1x on routed port
The example above describes how to enable dot1x on access port. This function can also enable on routed port. The following example shows how to change eth-0-25 to a routed port and enable dot1x.
Switch(config)# interface eth-0-25
Switch(config-if)# no switchport
Switch(config-if)# ip address 192.168.100.1/24
Switch(config-if)# dot1x port-control auto
Switch(config-if)# no shutdown
Switch(config-if)# exit
Using force mode
Dot1x port control mode can be force-authorized or force-unauthorized.
force-authorized:
Switch(config)# interface eth-0-25
Switch(config-if)# dot1x port-control force-authorized
Switch(config-if)# exit
force-unauthorized:
Switch(config)# interface eth-0-25
Switch(config-if)# dot1x port-control force-unauthorized
Switch(config-if)# exit
User can choose port control mode as force-authorized,force-unauthorized or auto. The final configuration should over write the previous one.
Enable dot1x accounting
Dot1x accounting can be used to keep track of network usage after user is authenticated. Dot1x accounting is disabled by default, you can enable it on globally configure mode.
Enable dot1x accounting:
Switch(config)# dot1x accounting-mode radius
Device sends accounting start request to server after user is authenticated when dot1x accounting is enabled, if no corresponding response is received, start-fail policy is needed:
online In order to avoid the impact of network failure on users, online policy can be configured to allow users to be online.
offline If dot1x accounting start fail, offline policy can be configured to reject users to be online .
Switch(config)# dot1x accounting start-fail online
User can configure realtime accounting to make device send realtime accounting request to server periodically. Server keeps accounting users only when received realtime accounting request, so that abnormal accounting can be avoided when server can not receive accounting stop packet from device.
Meanwhile, user can configure max times of realtime accounting with no response and the action when realtime accounting fails. By default, the max times of realtime accounting with no response is set to 3, and user is allowed to be online after realtime accounting failure.
Switch(config)# dot1x accounting realtime 60
Switch(config)# dot1x accounting interim-fail max-times 2 offline
dot1x optional parameter
Timer for Radius server: Set the wait time for re-activating RADIUS server; Set the maximum failed RADIUS requests sent to server; Set the timeout value for no response from RADIUS server.
Switch(config)# radius-server deadtime 10
Switch(config)# radius-server retransmit 5
Switch(config)# radius-server timeout 10
Interface attributes: Specify the number of reauthentication attempts before becoming unauthorized; Set the protocol version; Specify the quiet period in the HELD state; Enable reauthentication on a port; Specify the seconds between reauthorization attempts; Specify the authentication server response timeout; Specify the supplicant response timeout; Specify the Seconds between successive request ID attempts;
Enable dot1x handshake with client on a port; Specify the handshake period.
Switch(config)# interface eth-0-25
Switch(config-if)# dot1x max-req 5
Switch(config-if)# dot1x protocol-version 1
Switch(config-if)# dot1x quiet-period 120
Switch(config-if)# dot1x reauthentication
Switch(config-if)# dot1x timeout re-authperiod 1800
Switch(config-if)# dot1x timeout server-timeout 60
Switch(config-if)# dot1x timeout supp-timeout 60
Switch(config-if)# dot1x timeout tx-period 60
Switch(config-if)# dot1x handshake
Switch(config-if)# dot1x timeout handshake-period 1
Switch(config-if)# exit
Application cases
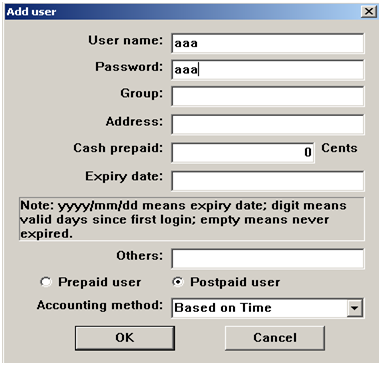
Radius server configuration (Using WinRadius for example)
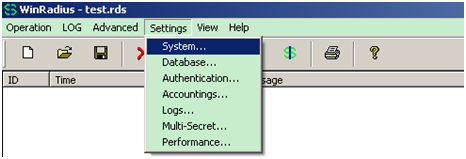
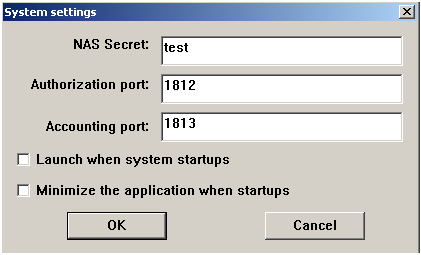
Fig. 7.8 Configure the shared-key, authorization port and account port