7.16. Configuring AAA
Overview
Function Introduction
Authentication verifies users before they are allowed access to the network and network services. System can use AAA authentication methods and Non-AAA authentication methods. RADIUS Authentication is one of AAA authentication methods. RADIUS is a distributed client/server system that secures networks against unauthorized access. RADIUS is widely used protocol in network environments. It is commonly used for embedded network devices such as routers, modem servers, switches, etc. RADIUS clients run on support routers and switches. Clients send authentication requests to a central RADIUS server, which contains all user authentication and network service access information.
Principle Description
N/A
Configuration
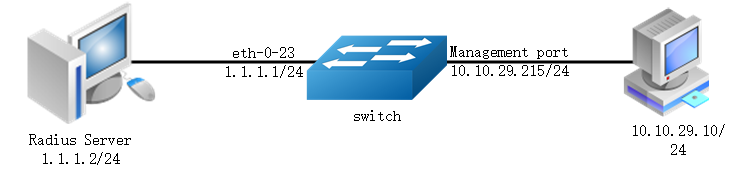
The figure above is the networking topology for RADIUS authentication functions. We need one Switch and two computers for this test.
One computer as RADIUS server, it ip address of the eth0 interface is 1.1.1.2/24.
Switch has RADIUS authentication function. The ip address of interface eth-0-23 is 1.1.1.1/24. The management ip address of switch is 10.10.29.215, management port is connected the PC for test login, PC’s ip address is 10.10.29.10.
step 1 Enter the configure mode
Switch# configure terminal
step 2 Enable AAA
Switch(config)# aaa new-model
Switch(config)# aaa authentication login default radius local
Switch(config)# aaa authorization exec default none
step 3 Configure Radius server
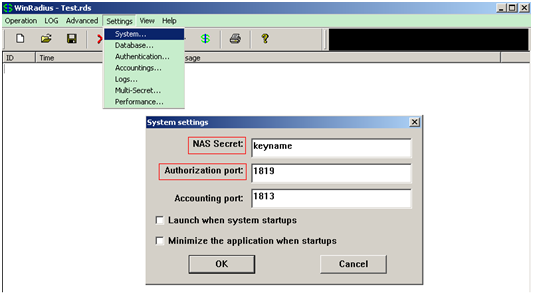
Switch(config)# radius-server host 1.1.1.2 auth-port 1819 key keyname
Switch(config)# radius-server host 2001:1000::1 auth-port 1819 key keyname
step 4 Configure a layer 3 interface and set ip address
Switch(config)# interface eth-0-23
Switch(config-if)# no switchport
Switch(config-if)# ip address 1.1.1.1/24
Switch(config-if)# quit
step 5 set authentication mode
Switch(config)# line vty 0 7
Switch(config-line)# login authentication default
Switch(config-line)# privilege level 4
Switch(config-line)# no line-password
step 6 Exit the configure mode
Switch(config-line)# end
step 7 Validation
You can use command show authentication status in switch:
Switch# show aaa status
aaa status:
Authentication enable
You can use command show keys in switch:
Switch# show aaa method-lists authentication
authen queue=AAA_ML_AUTHEN_LOGIN
Name = default state = ALIVE : local
Name = default state = ALIVE : radius local
Telnet output:

 Don’t forget to turn RADIUS authentication feature on.
Don’t forget to turn RADIUS authentication feature on.
Make sure the cables is linked correctly You can use command to check log messages if Switch can’t do RADIUS authentication:
Switch# show logging buffer
Application cases
Radius server configuration (Using WinRadius for example)
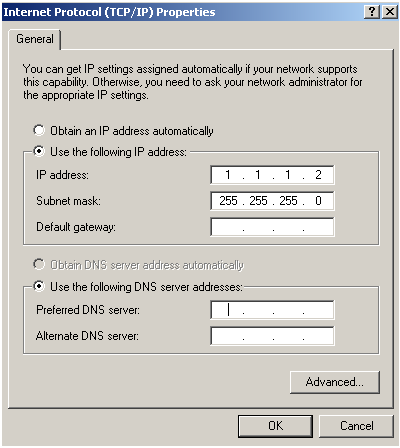
Set ip address for PC:
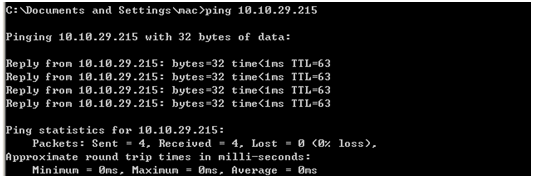
Connectivity test between server and switch:
Open winRadius:
Configurations for winRadius:
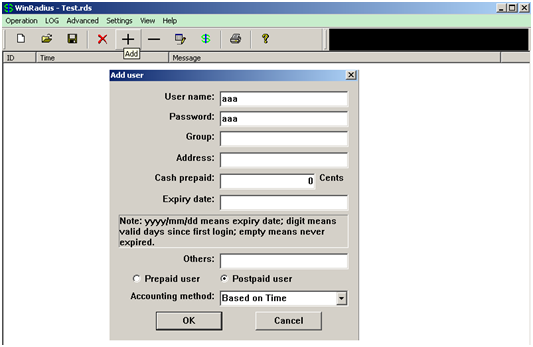
Add user and password:
Connectivity test between client and switch: