7.4. Configuring ACL
Overview
Function Introduction
Access control lists (ACLs) classify traffic with the same characteristics. The ACL can have multiple access control entries (ACEs), which are commands that match fields against the contents of the packet. ACLs can filter packets received on interface by many fields such as ip address, mac address and deny or permit the packets.
Principle Description
The following terms and concepts are used to describe ACL:
Access control entry (ACE): Each ACE includes an action element (permit or deny) and a series of filter element based on criteria such as source address, destination address, protocol, and protocol-specific parameters.
MAC ACL: MAC ACL can filter packet by mac-sa and mac-da, and the mac-address can be masked, or configured as host id, or configured as any to filter all MAC addresses. MAC ACL can also filter other L2 fields such as COS, VLAN-ID, INNER-COS, INNER-VLAN-ID, L2 type, L3 type.
IPv4 ACL: IPv4 ACL can filter packet by ip-sa and ip-da, and ip-address can be masked, or configured as host id, or configured as any to filter all IPv4 address. IPv4 ACL can also filter other L3 fields such as DSCP, L4 protocol and L4 fields such as TCP port, UDP port, and so on.
Time Range: Time range can define a period of time only between which the ACE can be valid if the ACE is associated to the time range.
Configuration
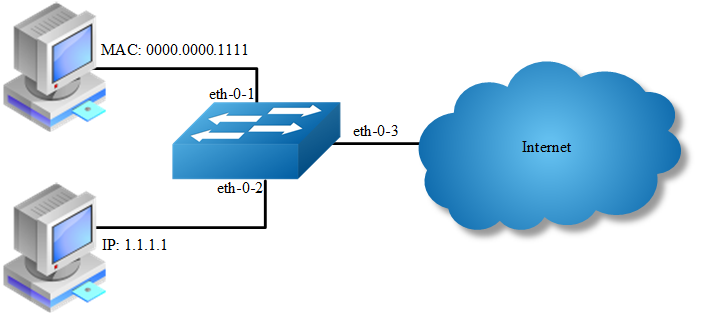
In this example, use MAC ACL on interface eth-0-1, to permit packets with source mac 0000.0000.1111 and deny any other packets. Use IPv4 ACL on interface eth-0-2, to permit packets with source ip 1.1.1.1/24 and deny any other packets.
step 1 Enter the configure mode
Switch# configure terminal
step 2 Create access list
MAC access list:
Switch(config)# mac access-list mac
Switch(config-mac-acl)# permit src-mac host 0000.0000.1111 dest-mac any
Switch(config-mac-acl)# deny src-mac any dest-mac any
Switch(config-mac-acl)# exit
IP access list:
Switch(config)# ip access-list ipv4
Switch(config-ip-acl)# permit any 1.1.1.1 0.0.0.255 any
Switch(config-ip-acl)# deny any any any
Switch(config-ip-acl)# exit
step 3 Create class-map, and bind the access list
Switch(config)# class-map cmap1
Switch(config-cmap)# match access-group mac
Switch(config-cmap)# exit
Switch(config)# class-map cmap2
Switch(config-cmap)# match access-group ipv4
Switch(config-cmap)# exit
step 4 Create policy-map and bind the class map
Switch(config)# policy-map pmap1
Switch(config-pmap)# class cmap1
Switch(config-pmap-c)# exit
Switch(config-pmap)# exit
Switch(config)# policy-map pmap2
Switch(config-pmap)# class cmap2
Switch(config-pmap-c)# exit
Switch(config-pmap)# exit
step 5 Apply the policy to the interface
Switch(config)# interface eth-0-1
Switch(config-if)# service-policy input pmap1
Switch(config-if)# exit
Switch(config-if)# interface eth-0-2
Switch(config-if)# service-policy input pmap2
Switch(config-if)# exit
step 6 Exit the configure mode
Switch(config)# end
step 7 Validation
The result of show running-config is as follows:
Switch# show running-config
mac access-list mac
10 permit src-mac host 0000.0000.1111 dest-mac any
20 deny src-mac any dest-mac any
!
ip access-list ipv4
10 permit any 1.1.1.0 0.0.0.255 any
20 deny any any any
!
class-map match-any cmap1
match access-group mac
!
class-map match-any cmap2
match access-group ipv4
!
policy-map pmap1
class cmap1
!
policy-map pmap2
class cmap2
!
interface eth-0-1
service-policy input pmap1
!
interface eth-0-2
service-policy input pmap2
!
Application cases
N/A