7.17. Configuring TACACS+
Overview
Function Introduction
Authentication verifies users before they are allowed access to the network and network services. System can use AAA authentication methods and Non-AAA authentication methods. TACACS+ Authentication is one of AAA authentication methods. TACACS+ is a distributed client/server system that secures networks against unauthorized access. TACACS+ is widely used protocol in network environments. It is commonly used for embedded network devices such as routers, modem servers, switches, etc. TACACS+ clients run on support routers and switches. Clients send authentication requests to a central TACACS+ server, which contains all user authentication and network service access information.
Principle Description
N/A
Configuration
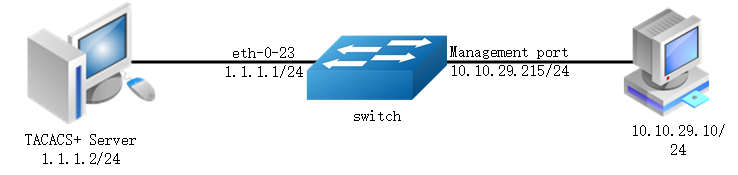
The figure above is the networking topology for TACACS+ authentication functions. We need one Switch and two computers for this test. One computer as TACACS+ server, it ip address of the eth0 interface is 1.1.1.2/24. Switch has TACACS+ authentication function. The ip address of interface eth-0-23 is 1.1.1.1/24. The management ip address of switch is 10.10.29.215, management port (only in-band management port) is connected the PC for test login, PC’s ip address is 10.10.29.10
step 1 Enter the configure mode
Switch# configure terminal
step 2 Enable AAA
Switch# configure terminal
Switch(config)# aaa new-model
Switch(config)# aaa authentication login tac-login tacacs-plus local
Switch(config)# aaa authorization exec default tacacs-plus
Switch(config)# aaa accounting exec default start-stop tacacs-plus
Switch(config)# aaa accounting commands default tacacs-plus
step 3 Configure tacacs+ server
Switch(config)# tacacs-server host 1.1.1.2 port 123 key keyname primary
step 4 Configure a layer 3 interface and set ip address
Switch(config)# interface eth-0-23
Switch(config-if)# no switchport
Switch(config-if)# ip address 1.1.1.1/24
Switch(config-if)# quit
step 5 set authentication mode
Switch(config)# line vty 0 7
Switch(config-line)# login authentication tac-login
Switch(config-line)# privilege level 4
Switch(config-line)# no line-password
step 6 Exit the configure mode
Switch(config-line) end
step 7 Validation
You can use command show authentication status in switch
Switch# show aaa status
aaa stats:
Authentication enable
You can use command show keys in switch:
Switch# show aaa method-lists authentication
authen queue=AAA_ML_AUTHEN_LOGIN
Name = default state = ALIVE : local
Name = tac-login state = ALIVE : tacacs-plus local
Telnet output:

Application cases
Radius server configuration
Download TACACS+ server code, DEVEL.201105261843.tar.bz2.
Build the TACACS+ server.
Add username and password in configure file.
!../obj.linux-2.6.9-89.29.1.elsmp-x86_64/tac_plus
id = spawnd {
listen = { port = 49 }
spawn = {
instances min = 1
instances max = 10
}
background = no
}
user = aaa {
password = clear bbb
member = guest
}
Run TACACS+ server:
[disciple: ~]$ ./tac_plus ./tac_plus.cfg.in -d 1
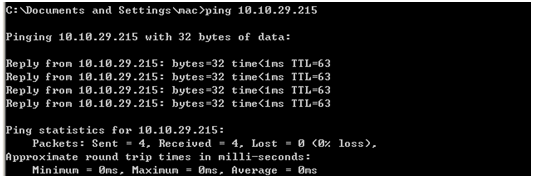
Use Ping command for test on PC: