13.2. Configuring EFD
Overview
Function Introduction
Elephant Flow Detect (EFD). According to the academic institutions of the actual network of the study found that more than 80% of the bandwidth is occupied by elephant flow, the bandwidth and transmission cache of these flow is large, but not sensitive to delay, which is sensitive to delay The flow caused a great impact. If elephant flow is recognized and some forwarding policies are implemented (such as reducing the forwarding priority of elephant flow appropriately, let mice flow be forwarded first), it can improve the transmission efficiency of network.
EFD function can be used to detect some abnormal traffic in the network (such as large bandwidth flow). After detecting, you can encapsulate the characteristics in the protocol packets and sent it to the specified server for further analysis.
Principle Description
terminology
EFD Elephant Flow Detect
Configuration
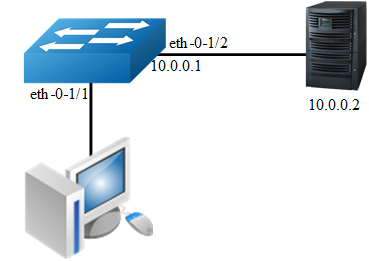
In the following example, it specifies the characteristics field and threshold of the traffic. When the flow rate exceed the specified threshold, the characteristics of the packets will be encapsulated into the user-defined UDP packets and sent to the server.
step 1 Enter the configure mode
Switch# configure terminal
step 1 Set the parameters for EFD
Specify ipda to calculate packet’s hash value
Switch(config)# hash-value global
Switch(config-hash-value-global)# efd select ipda
Configure the speed threshold of EFD. The flows which has the rate large than 1000Mbps will be marked as Elephant Flow. The default value is 50Mbps.
Switch(config)# efd detect speed 1000
Enable EFD notify feature, and specify the ipda and UDP port of notification packet
Switch(config)# efd notify enable 10.0.0.2 20007
step 3 Enter the interface configure mode and set the attributes of the interface
Switch(config)# interface eth-0-1/1
Switch(config-if)# efd enable
Switch(config-if)# exit
Switch(config)# int eth-0-1/2
Switch(config-if)# no switchport
Switch(config-if)# ip address 10.0.0.1/24
Switch(config-if)# exit
step 4 Create a static arp entry (Optional)
Switch(config)# arp 10.0.0.2 0.1.2
step 5 Exit the configure mode
Switch(config)# end
step 6 Validation
Switch# show efd configuration
Elephant flow detection configuration information:
--------------------------------------------------
Detect rate : 1000 Mbps
Detect granularity : 16B
Detect time interval : 1000 ms
EFD aging time : 120 ms ~ 150 ms
EFD detect packet type : All IP packets
EFD IPG : disable
EFD redirect interface : N/A
EFD flow hash fields : destination-ip
EFD enabled interface :
--------------------------------------------------
eth-0-1/1
When the flow received from eth-0-1 exceed 1000Mb, we can find this flow has been learned as EFD flow via the CLI below:
Switch# show efd flow information decap
EFD flow issued at:07:29:40 UTC Mon Aug 01 2023
From:eth-0-1, FlowId: 1701
-------------------------------------------------------
MACDA:0000.00aa.bbbb, MACSA:0000.00bb.bbbb
IPv4 Packet, IP Protocol is TCP(6)
IPDA:22.22.22.101, IPSA: 11.11.11.11
L4SourcePort:43690, L4DestinationPort:43741
-------------------------------------------------------
00 00 00 aa bb bb 00 00 00 bb bb bb 08 00 45 00
00 32 00 00 40 00 c8 06 70 35 0b 0b 0b 0b 16 16
16 65 aa aa aa dd aa aa aa dd aa aa aa dd aa aa
aa dd aa aa aa dd aa aa aa dd aa aa aa dd aa aa
Server 10.0.0.2 Tcpdump result:
12:41:28.286993 92:fd:58:d7:8f:00 > 00:00:00:01:00:02, ethertype IPv4
(0x0800), length 60: IP (tos 0x0, ttl 64, id 0, offset 0, flags
[DF], proto 17, length: 44) 10.0.0.1.49071 > 10.0.0.2.20007: [udp
sum ok] UDP, length 16
0x0000: 0000 0001 0002 92fd 58d7 8f00 0800 4500 ........X.....E.
0x0010: 002c 0000 4000 4011 26bf 0a00 0001 0a00 .,..@.@.&.......
0x0020: 0002 bfaf 4e27 0018 b05b 0000 0101 0000 ....N'...[......
0x0030: 0008 0001 0004 1616 1665 0000 .........e..
 EFD packet head description. The red part above is part of EFD packet information, specific analysis is as follows:
EFD packet head description. The red part above is part of EFD packet information, specific analysis is as follows:
0000: reserved, no specific meaning. Part of EFD packet head.
01:EFD packt version number, only support 0x01. Part of EFD packet head.
01:EFD flow opcode, 0x01: This flow is first recognized as elephant flow. 0x02: This flow has been recognized as elephant flow before. Part of EFD packet head.
0000 0008: EFD packet data part length(include data part type). Part of EFD packet head.
0001: EFD packet data part type. 0x0001 means data part is IPDA.
0004: EFD packet data part length.
16161665:date part, means IPDA is 22.22.22.101
Application cases
N/A