10.2. Configuring IPv4 GRE Tunnel
Overview
Function Introduction
Tunneling is an encapsulation technology, which uses one network protocol to encapsulate packet of another network protocol and transfer them over a virtual point to point connection. The virtual connection is called a tunnel. Tunneling refers to the whole process from data encapsulation to data transfer to data de-encapsulation.
Principle Description
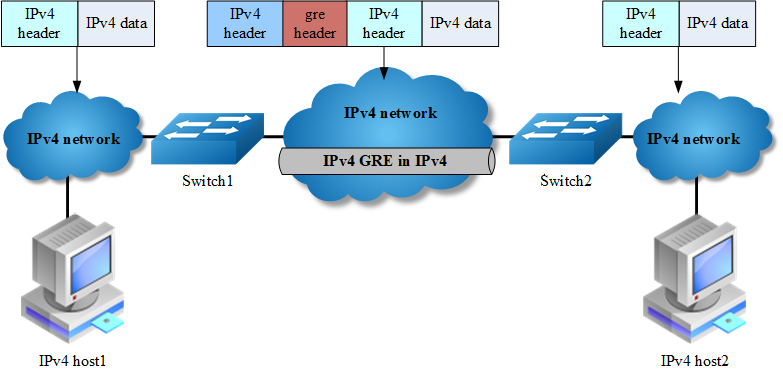
When it is required to communicate with isolated IPv4 networks, you should create a tunnel mechanism between them. The tunnel with transmit protocol of gre connected with two isolated IPv4 island is called IPv4 gre tunnel, which is that IPv4 packets are encapsulated by gre protocol over outer IPv4 packets. Gre tunnel would add gre head in encapsulated packets, including key, sequence, checksum and so on. In order to make an implement of gre tunnel, both tunnel endpoints must support the IPv4 protocol stacks.
IPv4 gre tunnel processes packets in the following ways:
A host in the IPv4 network sends an IPv4 packet to Switch1 at the tunnel source.
After determining according to the routing table that the packet needs to be forwarded through the tunnel, Switch1 encapsulates the IPv4 packet with an IPv4 header and forwards it through the physical interface of the tunnel.
Upon receiving the packet, Switch2 de-encapsulates the packet.
Switch2 forwards the packet according to the destination address in the de-encapsulated IPv4 packet. If the destination address is the device itself, Switch2 forwards the IPv4 packet to the upper-layer protocol for processing. In the process of de-encapsulation, it would check gre key, only the matched key of packet can be processed, otherwise discarded.
The ip address of tunnel source and tunnel destination is manually assigned, and it provides point-to-point connection. By using overlay tunnels, you can communicate with isolated IPv4 networks without upgrading the IPv4 infrastructure between them. Overlay tunnels can be configured between border routers or between border routers and a host.
The primary use is for stable connections that require regular secure communication between two edge routers or between an end system and an edge router, or for connection to remote IPv4 networks, gre key is alternative configuration.
Configuration
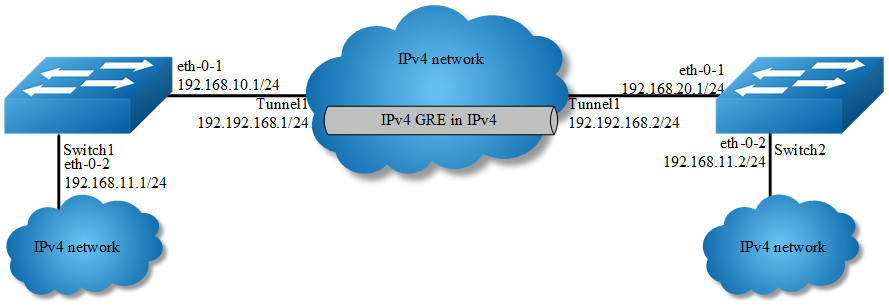
As the topology shows, two IPv4 networks connect to the network via Switch1 and Switch2. An Ipv4 gre tunnel is required between Switch1 and Switch2, in order to connect two networks.
 A reachable Ipv4 route is necessary for forwarding tunnel packet. Ipv4 address must be configured on tunnel interface; otherwise the route via this tunnel interface is invalid.
A reachable Ipv4 route is necessary for forwarding tunnel packet. Ipv4 address must be configured on tunnel interface; otherwise the route via this tunnel interface is invalid.
The following configuration should be operated on all switches if the switch ID is not specified.
step 1 Enter the configure mode
Switch# configure terminal
step 2 Enter the interface configure mode and set the attributes of the interface
Interface configuration for Switch1:
Switch(config)# interface eth-0-1
Switch(config-if)# no switchport
Switch(config-if)# no shutdown
Switch(config-if)# ip address 192.168.10.1/24
Switch(config-if)# tunnel enable
Switch(config-if)# exit
Switch(config)# interface eth-0-2
Switch(config-if)# no switchport
Switch(config-if)# no shutdown
Switch(config-if)# ip address 192.168.11.1/24
Switch(config-if)# exit
Interface configuration for Switch2:
Switch(config)# interface eth-0-1
Switch(config-if)# no switchport
Switch(config-if)# no shutdown
Switch(config-if)# ip address 192.168.20.1/24
Switch(config-if)# tunnel enable
Switch(config-if)# exit
Switch(config)# interface eth-0-2
Switch(config-if)# no switchport
Switch(config-if)# no shutdown
Switch(config-if)# ip address 192.168.12.1/24
Switch(config-if)# exit
step 3 Configure the tunnel interface
Tunnel interface configuration for Switch1:
Switch(config)# interface tunnel1
Switch(config-if)# tunnel mode gre
Switch(config-if)# tunnel source eth-0-1
Switch(config-if)# tunnel destination 192.168.20.1
Switch(config-if)# tunnel gre key 100
Switch(config-if)# ip address 192.192.168.1/24
Switch(config-if)# keepalive 5 3
Switch(config-if)# exit
Tunnel interface configuration for Switch2:
Switch(config)# interface tunnel1
Switch(config-if)# tunnel mode gre
Switch(config-if)# tunnel source eth-0-1
Switch(config-if)# tunnel destination 192.168.10.1
Switch(config-if)# tunnel gre key 100
Switch(config-if)# ip address 192.192.168.2/24
Switch(config-if)# keepalive 5 3
Switch(config-if)# exit
step 4 Configure the static route and arp
Configuring Switch1:
Switch(config)# ip route 192.168.20.0/24 192.168.10.2
Switch(config)# ip route 192.168.12.0/24 tunnel1
Configuring Switch2:
Switch(config)# ip route 192.168.10.0/24 192.168.20.2
Switch(config)# ip route 192.168.11.0/24 tunnel1
step 5 Exit the configure mode
Switch(config)# end
step 6 Validation
Display the result on Switch1:
Switch# show interface tunnel1
Interface tunnel1
Interface current state: UP
Hardware is Tunnel
Index 8193 , Metric 1 , Encapsulation TUNNEL
VRF binding: not bound
Internet primary address:
192.192.168.1/24 pointopoint 192.192.168.255
Tunnel protocol/transport GRE/IP, Status Valid
Tunnel source 192.168.10.1(eth-0-1), destination 192.168.20.1
Tunnel DSCP inherit, Tunnel TTL 255
Tunnel GRE key enable: 100
Tunnel GRE keepalive enable, Send period: 5, Retry times: 3
0 packets input, 0 bytes
0 packets output, 0 bytes
Display the result on Switch2:
Switch# show interface tunnel1
Interface tunnel1
Interface current state: UP
Hardware is Tunnel
Index 8193 , Metric 1 , Encapsulation TUNNEL
VRF binding: not bound
Internet primary address:
192.192.168.2/24 pointopoint 192.192.168.255
Tunnel protocol/transport GRE/IP, Status Valid
Tunnel source 192.168.20.1(eth-0-1), destination 192.168.10.1
Tunnel DSCP inherit, Tunnel TTL 255
Tunnel GRE key enable: 100
Tunnel GRE keepalive enable, Send period: 5, Retry times: 3
0 packets input, 0 bytes
0 packets output, 0 bytes
Application cases
N/A