7.14. Configuring IP source guard
Overview
Function Introduction
IP source guard prevents IP spoofing by allowing only the IP addresses that are obtained through DHCP snooping on a particular port. Initially, all IP traffic on the port is blocked except for the DHCP packets that are captured by DHCP snooping. When a client receives a valid IP address from the DHCP server, an access control list (ACL) is installed on the port that permits the traffic from the IP address. This process restricts the client IP traffic to those source IP addresses that are obtained from the DHCP server; any IP traffic with a source IP address other than that in the ACL’s permit list is filtered out. This filtering limits the ability of a host to attack the network by claiming a neighbor host’s IP address.
IP source guard uses source IP address filtering, which filters the IP traffic that is based on its source IP address. Only the IP traffic with a source IP address that matches the IP source binding entry is permitted. A port’s IP source address filter is changed when a new DHCP-snooping binding entry for a port is created or deleted. The port ACL is modified and reapplied in the hardware to reflect the IP source binding change. By default, if you enable IP source guard without any DHCP-snooping bindings on the port, a default ACL that denies all IP traffic is installed on the port. When you disable IP source guard, any IP source filter ACL is removed from the port.
Also IP source guard can use source IP and MAC address Filtering. When IP source guard is enabled with this option, IP traffic is filtered based on the source IP and Mac addresses. The switch forwards traffic only when the source IP and MAC addresses match an entry in the IP source binding table. If not, the switch drops all other types of packets except DHCP packet.
The switch also supports to have IP, MAC and VLAN Filtering. When IP source guard is enabled with this option, IP traffic is filtered cased on the source IP and MAC addresses. The switch forwards traffic only when the source IP, MAC addresses and VLAN match an entry in the IP source binding table.
When ip source guard is enabled on an interface, enable arp as-layer-3 in global configuration mode so that arp packets matching ip source guard entries can be forwarded normally.If it is disable, the system is discarded, affecting network communication.
Principle Description
The following terms and concepts are used to describe the IP source guard:
Dynamic Host Configuration Protocol (DHCP): Dynamic Host Configuration Protocol (DHCP) is a client/server protocol that automatically provides an Internet Protocol (IP) host with its IP address and other related configuration information such as the subnet mask and default gateway.
DHCP Snooping: DHCP snooping is a security feature that acts like a firewall between untrusted hosts and trusted DHCP servers. This feature builds and maintains the DHCP snooping binding database, which contains information about untrusted hosts with leased IP addresses.
ACL: Access control list.
Configuration
Configure ip source guard
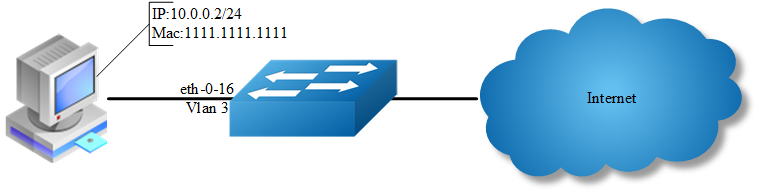
step 1 Enter the configure mode
Switch# configure terminal
step 2 Enable arp as-layer-3
Switch(config)# arp as-layer-3 enable
step 3 Enter the vlan configure mode and create vlan
Switch(config)# vlan database
Switch(config-vlan)# vlan 3
Switch(config-vlan)# exit
step 4 Enter the interface configure mode and set the attributes
Switch(config)# interface eth-0-16
Switch(config-if)# switchport
Switch(config-if)# no shutdown
Switch(config-if)# switchport access vlan 3
Switch(config-if)# exit
step 5 Add IP source guard entries
Switch(config)# ip source maximal binding number per-port 15
Switch(config)# ip source binding mac 1111.1111.1111 vlan 3 ip 10.0.0.2 interface eth-0-16
step 6 Enable IP source guard on the interface
Switch(config)# interface eth-0-16
Switch(config-if)# ip verify source ip
Switch(config-if)# exit
step 7 Exit the configure mode
Switch(config)# exit
step 8 Validation
Switch# show running-config interface eth-0-16
!
interface eth-0-16
ip verify source ip
switchport access vlan 3
Remove ip source guard entries
Remove by entry
Switch(config)# no ip source binding mac 1111.1111.1111 vlan 3 ip 10.0.0.2 interface eth-0-16
Remove by interface
Switch(config)# no ip source binding entries interface eth-0-16
Remove by vlan:
Switch(config)# no ip source binding entries vlan 3
Remove all:
Switch(config)# no ip source binding entries
Application cases
N/A