7.12. Configuring ARP Inspection
Overview
Function Introduction
ARP inspection is a security feature that validates ARP packets in a network. ARP inspection intercepts, logs, and discards ARP packets with invalid IP-to-MAC address bindings. This capability protects the network from some man-in-the-middle attacks. ARP inspection ensures that only valid ARP requests and responses are relayed. The switch performs these activities:
Intercept all ARP requests and responses on untrusted ports.
Verify that each of these intercepted packets has a valid IP-to-MAC address binding before updating the local ARP cache or before forwarding the packet to the appropriate destination.
Drop invalid ARP packets.
ARP inspection determines the validity of an ARP packet based on valid IP-to-MAC address bindings stored in a trusted database, the DHCP snooping binding database. This database is built by DHCP snooping if DHCP snooping is enabled on the VLANs and on the switch. If the ARP packet is received on a trusted interface, the switch forwards the packet without any checks. On entrusted interfaces, the switch forwards the packet only if it is valid.
Principle Description
Following is a brief description of terms and concepts used to describe the ARP Inspection:
DHCP Snooping: DHCP snooping is a security feature that acts like a firewall between untrusted hosts and trusted DHCP servers. This feature builds and maintains the DHCP snooping binding database, which contains information about untrusted hosts with leased IP addresses.
Address Resolution Protocol (ARP): ARP provides IP communication within a Layer 2 broadcast domain by mapping an IP address to a MAC address. For example, Host B wants to send information to Host A, but it does not have the MAC address of Host A in its ARP cache. Host B generates a broadcast message for all hosts within the broadcast domain to obtain the MAC address associated with the IP address of Host A. All hosts within the broadcast domain receive the ARP request, and Host A responds with its MAC address.
Configuration
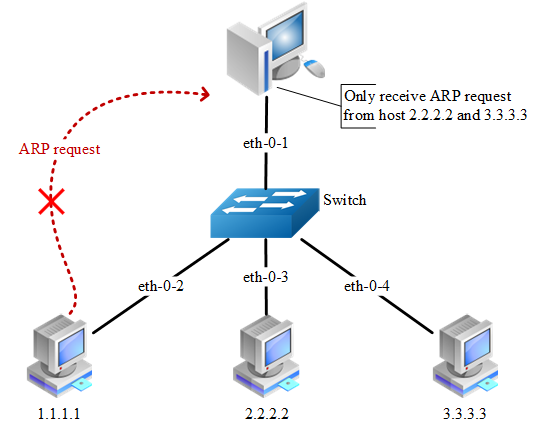
step 1 Enter the configure mode
Switch# configure terminal
step 2 Enter the vlan configure mode and create vlan
Switch(config)# vlan database
Switch(config-vlan)# vlan 2
Switch(config-vlan)# exit
Switch(config)# exit
step 3 Enter the interface configure mode, add the interface into the vlan
Switch(config)# interface eth-0-1
Switch(config-if)# switchport access vlan 2
Switch(config-if)# exit
Switch(config)# interface eth-0-2
Switch(config-if)# switchport access vlan 2
Switch(config-if)# exit
Switch(config)# interface eth-0-3
Switch(config-if)# switchport access vlan 2
Switch(config-if)# exit
Switch(config)# interface eth-0-4
Switch(config-if)# switchport access vlan 2
Switch(config-if)# exit
step 4 Configure arp inspection
Switch(config)# interface eth-0-1
Switch(config-if)# ip arp inspection trust
Switch(config-if)# exit
Switch(config)# ip arp inspection vlan 2
Switch(config)# ip arp inspection validate src-mac ip dst-mac
step 5 Configure arp access list
Switch(config)# arp access-list test
Switch(config-arp-acl)# deny request ip host 1.1.1.1 mac any
Switch(config-arp-acl)# exit
Switch(config)# ip arp inspection filter test vlan 2
step 6 Exit the configure mode
Switch(config)# exit
step 7 Validation
Check the configuration of ARP Inspection on switch:
Switch# show ip arp inspection
Source Mac Validation : Enabled
Destination Mac Validation : Enabled
IP Address Validation : Enabled
Vlan Configuration ACL Match Static ACL
=================================================================
2 enabled test
Vlan ACL Logging DHCP Logging
=================================================================
2 deny deny
Vlan Forwarded Dropped DHCP Drops ACL Drops
=================================================================
2 0 0 0 0
Vlan DHCP Permits ACL Permits Source MAC Failures
=================================================================
2 0 0 0
Vlan Dest MAC Failures IP Validation Failures Invalid Protocol Data
=================================================================
2 0 0 0
Show the log information of ARP Inspection on switch:
Switch# show ip arp inspection log
Total Log Buffer Size : 32
Syslog rate : 5 entries per 1 seconds.
1970-01-02 00:30:47 : Drop an ARP packet by ACL on vlan 2
1970-01-02 00:30:47 : Drop an ARP packet by ACL on vlan 2
1970-01-02 00:30:47 : Drop an ARP packet by ACL on vlan 2
1970-01-02 00:30:47 : Drop an ARP packet by ACL on vlan 2
1970-01-02 00:30:47 : Drop an ARP packet by ACL on vlan 2
1970-01-02 00:30:47 : Drop an ARP packet by ACL on vlan 2
1970-01-02 00:30:47 : Drop an ARP packet by ACL on vlan 2
1970-01-02 00:30:47 : Drop an ARP packet by ACL on vlan 2
1970-01-02 00:30:47 : Drop an ARP packet by ACL on vlan 2
1970-01-02 00:30:47 : Drop an ARP packet by ACL on vlan 2
1970-01-02 00:30:47 : Drop an ARP packet by ACL on vlan 2
Application cases
N/A