7.1. Configuring Port Security
Overview
Function Introduction
Port security feature is used to limit the number of “secure” MAC addresses learnt on a particular interface. The interface will forward packets only with source MAC addresses that match these secure addresses. The secure MAC addresses can be created manually, or learnt automatically. After the number of secure MAC addresses reaches the limit for the number of secure MAC addresses, new MAC address can’t be learnt or configured on the interface. if the interface then receives a packet with a source MAC address that is different with any of the secure addresses, it is considered as a security violation and should be discarded.
Port security feature also binds a MAC to a port so that the port does not forward packets with source addresses that are outside of defined addresses. If a MAC addresses configured or learnt on a secure port attempts to access another port, this is also considered as a security violation.
Two types of secure MAC addresses are supported:
Static secure MAC addresses: These are manually configured by the interface configuration command “switchport port-security mac-address”.
Dynamic secure MAC addresses: These are dynamically learnt.
If a security violation occurs, the packets to be forwarded will be dropped. User can configure the action by command “switchport port-security violation”. There are three actions can be chosen
errdisable: discard the packet and set the port to errdisable status. Please reference to Ethernet configuration guide, chapter errdisable.
protect: discard only.
restrict discard and record the event in log.
Principle Description
N/A
Configuration
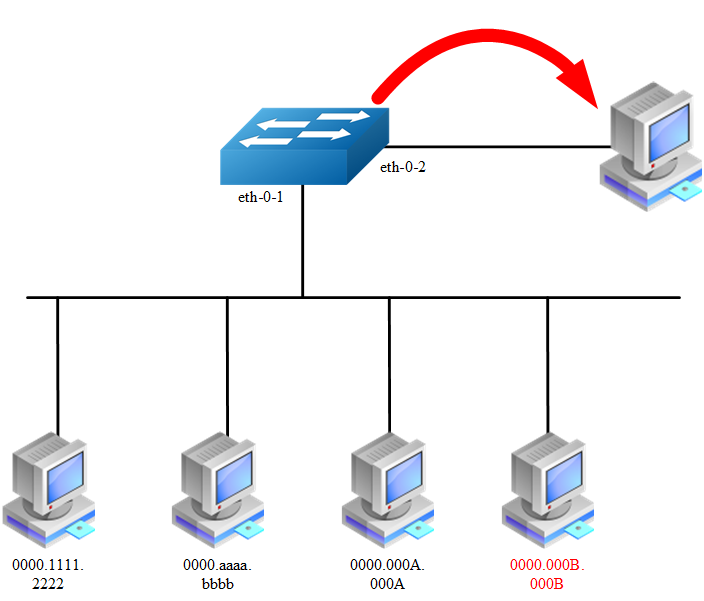
According to the topology above, only receive three Mac entries and discard source mac 0000.000B.000B after the following configuration:
step 1 Enter the configure mode
Switch# configure terminal
step 2 Enter the interface configure mode set the attributes, and enable pim-sm
Switch(config)# interface eth-0-1
Switch(config-if)# switchport
Switch(config-if)# switchport port-security
Switch(config-if)# switchport port-security maximum 2
Switch(config-if)# switchport port-security mac-address 0000.1111.2222 vlan 1
Switch(config-if)# switchport port-security violation restrict
Switch(config-if)# exit
step 3 Exit the configure mode
Switch(config)# end
step 4 Validation
Switch# show port-security
Secure Port MaxSecureAddr CurrentAddr SecurityViolationMode
(Count) (DynamicCount)
--------------------------------------------------------------------
eth-0-1 2 2 restrict
Switch# show port-security address-table
Secure MAC address table
---------------------------------------------------------------------
Vlan Mac Address Type Ports
---- ----------- ---- ------
1 0000.1111.2222 SecureConfigured eth-0-1
1 0000.aaaa.bbbb SecureLearned eth-0-1
1 0000.000a.000a SecureLearned eth-0-1
Switch# show port-security interface eth-0-1
Port security : enabled
Violation mode : discard packet and log
Maximum dynamic MAC addresses : 2
Total MAC addresses : 3
Static configured MAC addresses : 1
Application cases
N/A